Hands-on how to deploy Microsoft Defender for Endpoint ATP for macOS with VMware Workspace ONE UEM (AirWatch).
Introduction
Microsoft is good in positioning and selling their products & suites. As a result more and more enterprises want or have to use Microsoft Defender for Endpoint ATP (Advanced Threat Protection). In my customer scenario I was asked to deploy and pre-configure the Microsoft ATP client for macOS Catalina 10.15.4 with VMware Workspace ONE (WS1) UEM solution. The tests have been done in 2020-05 time.
Index & Version Info
### Index
Good to know before
Step 1: WS1 UEM - Required Profiles
Step 2: macOS Client - Tests Before App Deployment
Step 3: WS1 UEM - App Configuration
Step 4: macOS Client - Tests After App Deployment
Helpful URLs
### Version Info
- 2020-12-26: Added "Good to know before" section
### About the Author
Oliver Kluenter - Vita URL here - Contact me to discuss on LinkedIn hereGood to know before
### Good to know before
# macOS 10.15 and higher required on devices
- Microsoft Defender ATP client uses macOS System Extensions + Kernel Extensions
- Configuring apps utilizing System Extensions (SEXT) requires macOS 10.15+
- System Extension are the current way to go for security app developers in order to gain required permissions and execute their background task
- Using UEM SEXT payload policies is the best practice from Microsoft
=> Deploy Microsoft WDAV/ATP client on macOS 10.15 and higher - users with lower OS need to upgradeStep 1: WS1 UEM – Required Profiles
The use case was successfully tested end-to-end with a macOS Fusion VM. You can put all required payloads into a single device-based macOS profile. The UEM profiles will be used for #A: OS specific policy configurations (KEXT, SEXT, Provacy Prefences) and #B: pre-configuration of Microsoft WDAV and ATP settings (2x Custom Settings).
#1: KERNEL EXTENSION (KEXT)
- FYI: KEXT requires macOS 10.13.2+
- Allowed team Identifiers: team identifier UBF8T346G9
- Optional: Allowed Kernel Extensions: team identifier UBF8T346G9 | Bundle ID: com.microsoft.wdav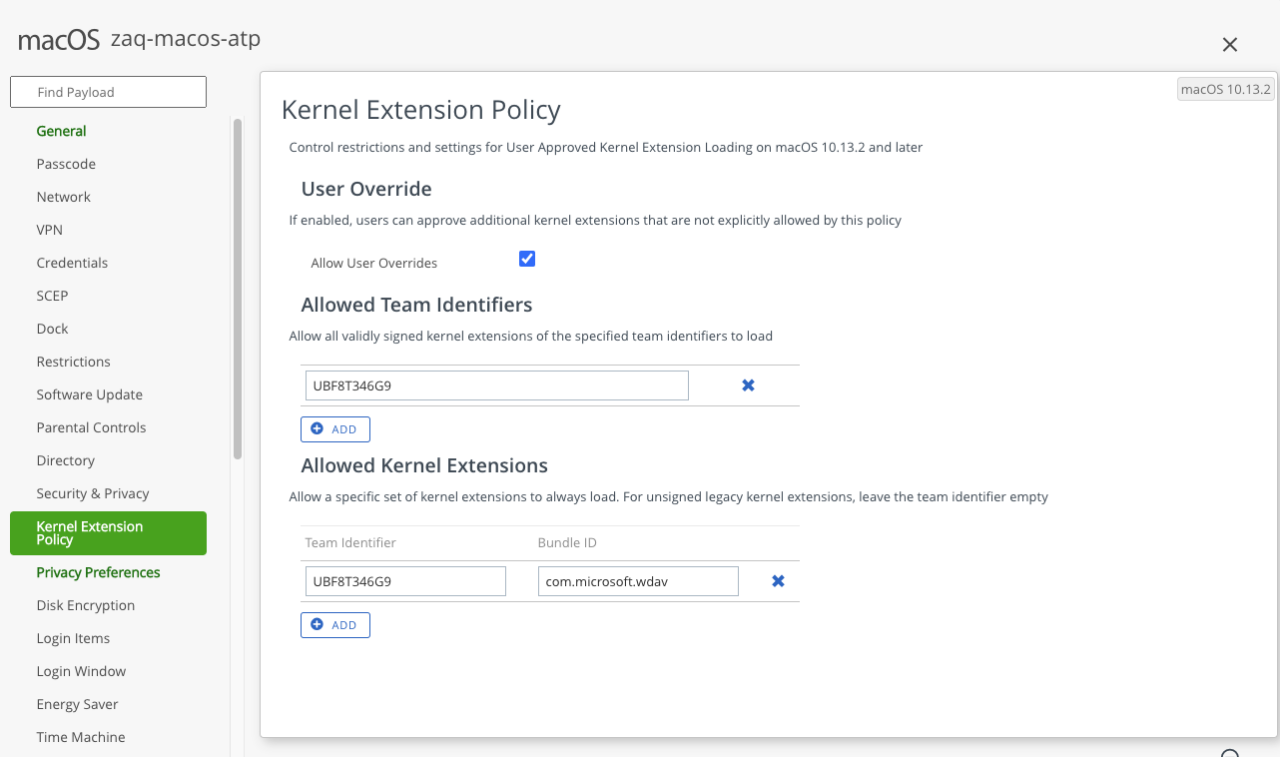
#2: SYSTEM EXTENSION (SEXT) POLICY
- FYI: SEXT requires macOS 10.15+
- [Allow User Overrides:yes/no]
# Allowed System Extension types -> add “+ system extension type” entry
- Team Identifier: UBF8T346G9
- Check mark “Endpoint Security"
- Allowed System Extensions: team identifier UBF8T346G9 | Bundle ID: com.microsoft.wdav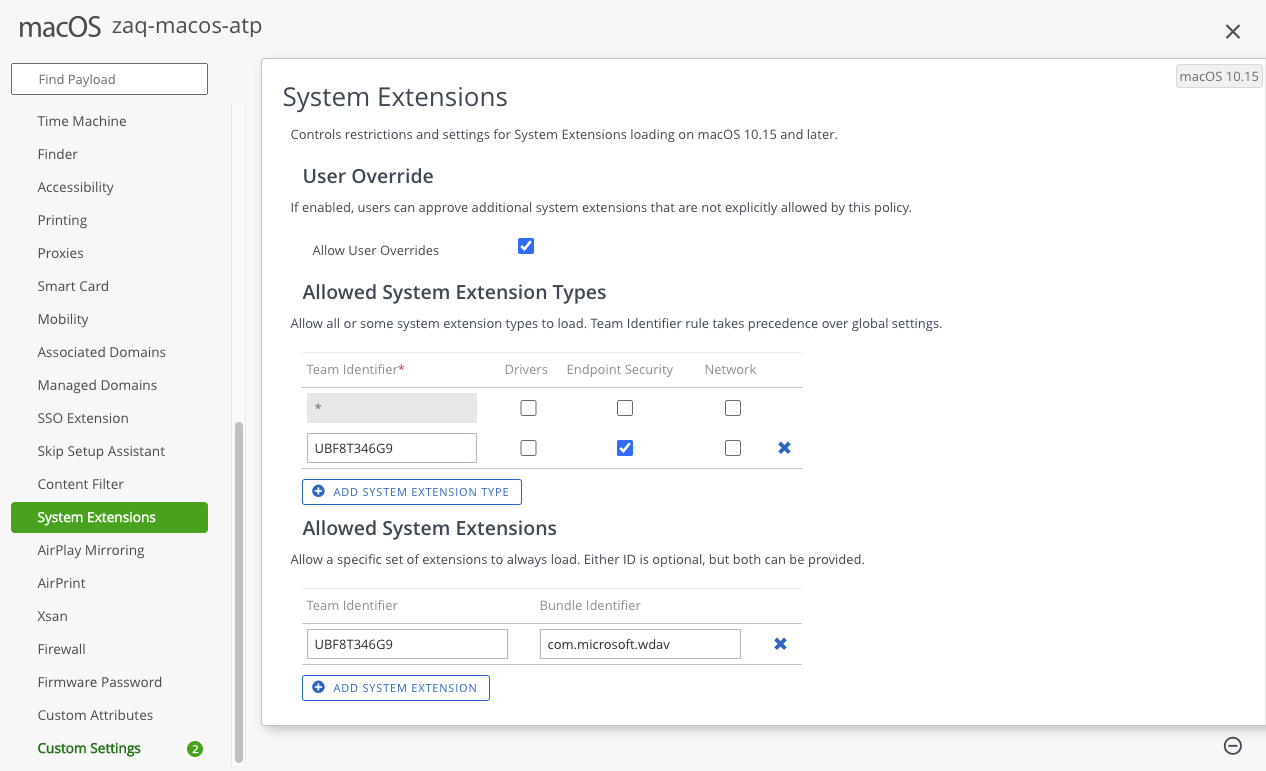
#3: PRIVACY PREFERENCES
- FYI: Privacy Preferences requires macOS 10.14+ with User Accepted MDM
- [Bundle] Identifier = com.microsoft.wdav
- Identifier Type: "Bundle ID"
- Code Requirement = identifier "com.microsoft.wdav" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UBF8T346G9
- System Policy All Files = Allow
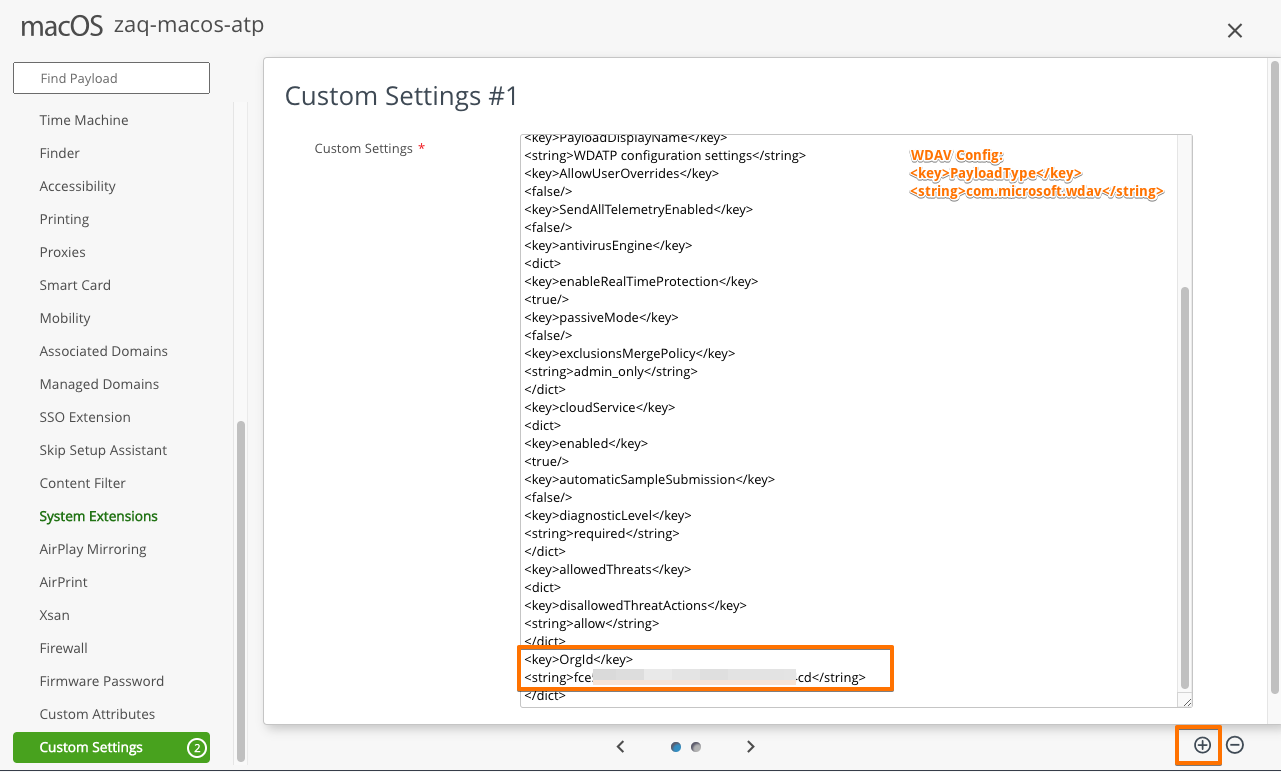
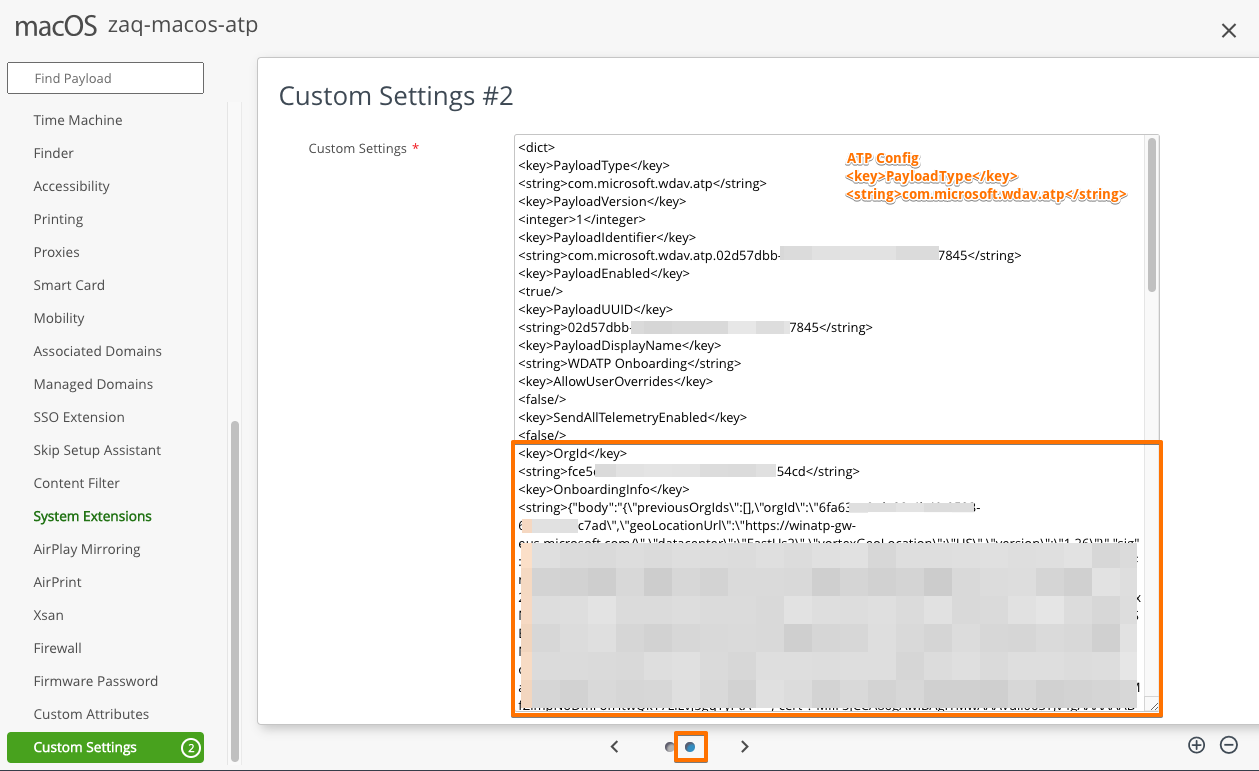
#4: 2x CUSTOM SETTINGS PAYLOADS
- Process reference docs to cross check: Deploying Microsoft Defender for Endpoint for macOS with Jamf Pro - URL HERE
- Windows Security Center: You require Microsoft 365 Enterprise subscription. Any EMS E plan is not good enough
- Download Microsoft “Onboarding Package" for your ATP tenant from Windows Security Center URL HERE => Device Management teams may need to contact their Security team
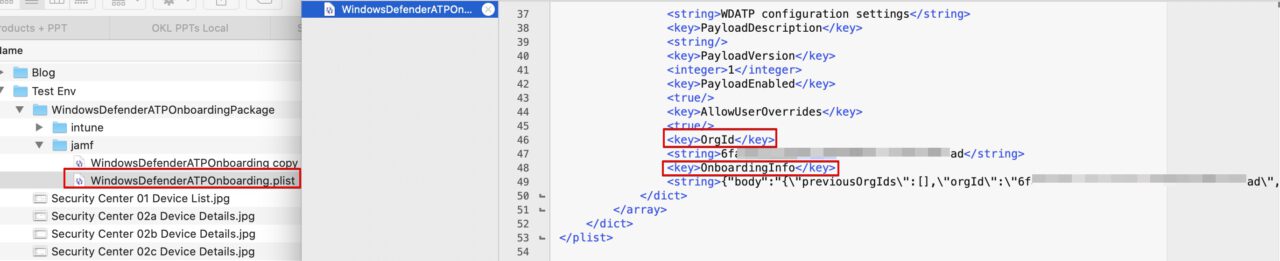
- Unzip and open the WindowsDefenderATPOnboarding.plist file in the JAMF folder
- Search/copy+paste <key>OrgId</key> and <key>OnboardingInfo</key>
- Create the 2 WS1 UEM Custom Settings payloads by following VMware macOS Samples URL and copy/paste the <key>OrgId</key> and <key>OnboardingInfo</key> where required
- Yes, the Onboarding info string is longer than 4.000 chars - don't wonder
- Create your own payload UUIDs for macOS Custom Setting payload https://www.uuidgenerator.net/ Step 2: macOS Client – Tests Before App Deployment
You can deploy the profile to the device in advance and trouble shoot if the profile is alreay received in the device.
# macOS - Profile Check
Cross check if the Profile was deployed correctly in
A) System Preferences / Profiles => look for payload
B) Drive / Library / Managed Prefences => look for com.microsoft.wdav + com.microsoft.wdav.atp PLIST files
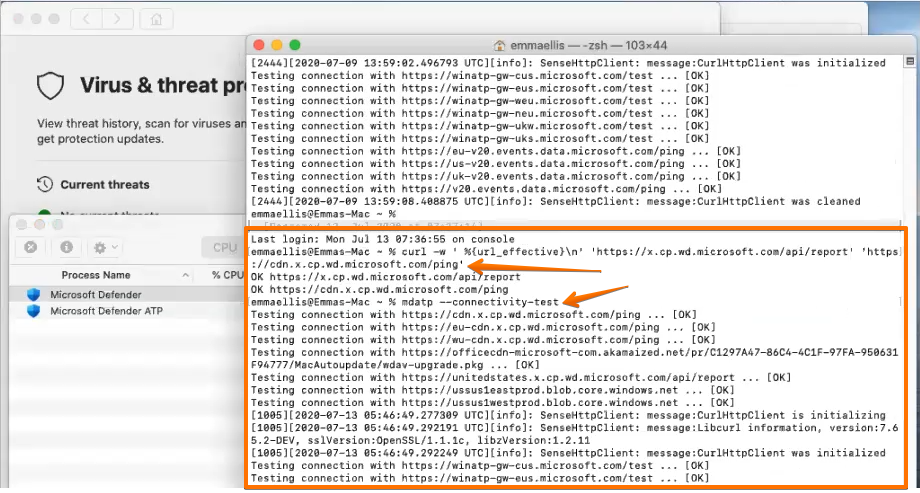
# ATP Network Tests: To test that required outgoing connections are not blocked, open https://x.cp.wd.microsoft.com/api/report and https://cdn.x.cp.wd.microsoft.com/ping in a browser
or via BASH: $ curl -w ' %{url_effective}\n' 'https://x.cp.wd.microsoft.com/api/report' 'https://cdn.x.cp.wd.microsoft.com/ping’Step 3: WS1 UEM – App Configuration
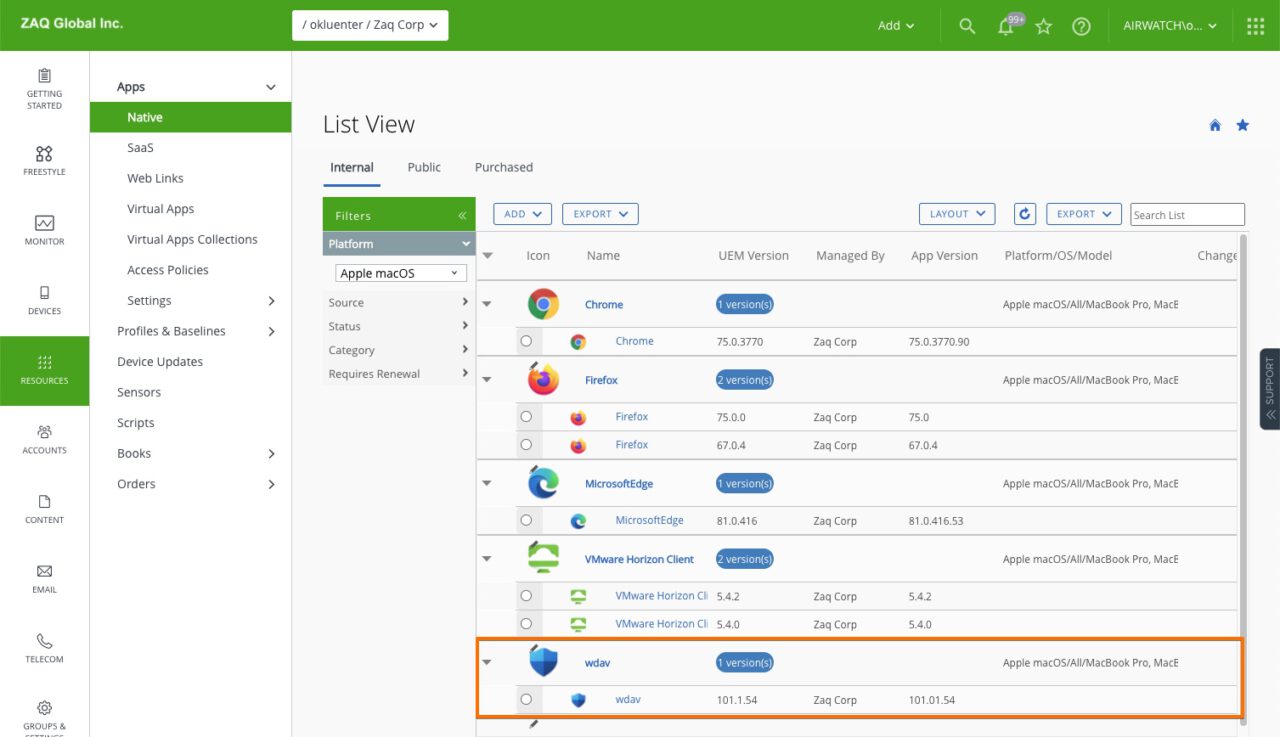
# Get VMware Assistant Packaging Tool to create WS1 UEM deployment metadata
https://resources.workspaceone.com/view/sglgk6r58lbn92jsyqky/en
# How to get Microsoft Defender installer and onboading configuration files
- Download Microsoft “Onboarding Package" for your ATP tenant from Windows Security Center - URL HERE
- Download "installation package" => wdav.pkg
- Once you have the wdav.pkg, it is straight forward with WS1 UEM processes
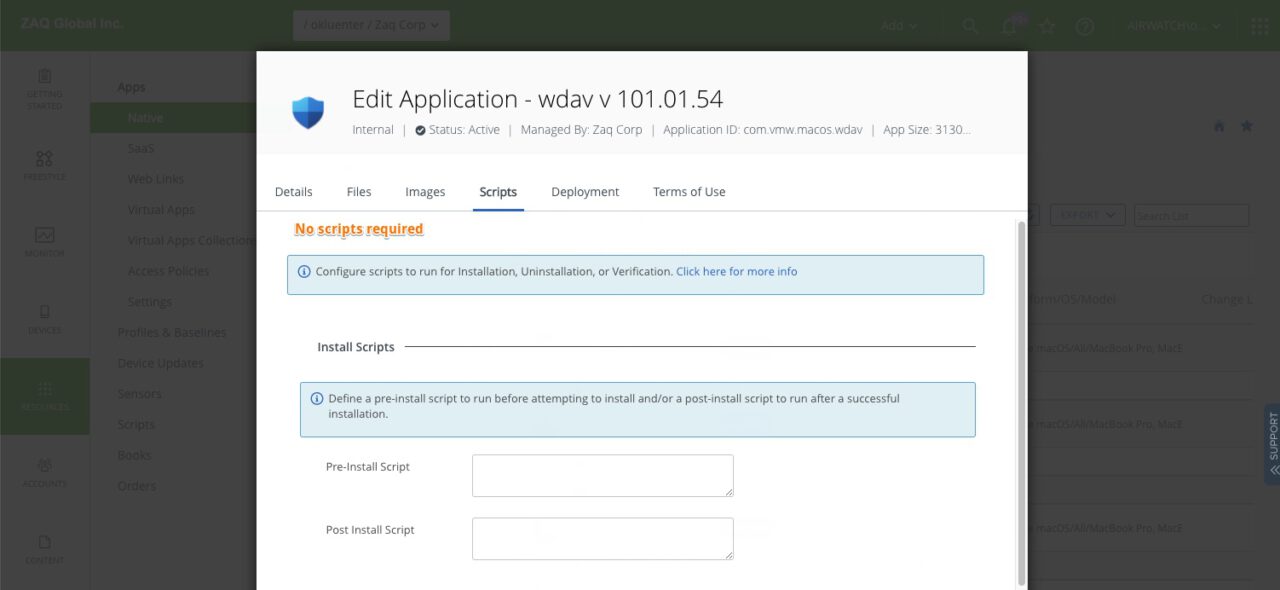
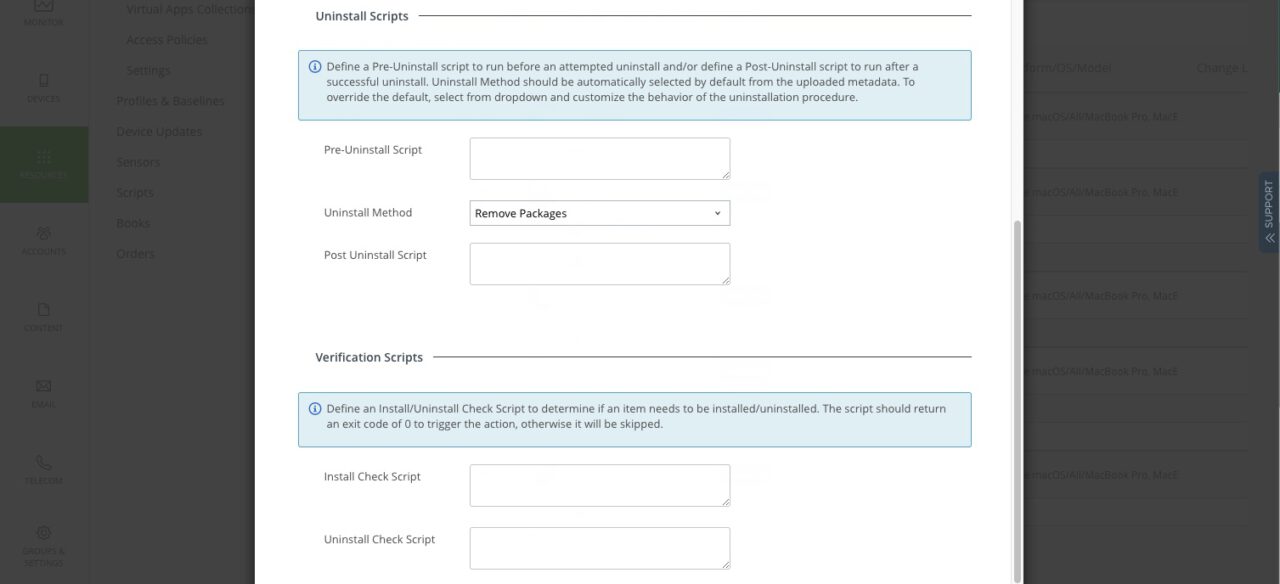
- no additional WS1 UEM pre/post scripts needed for installation / de-installation
- Assignment: You may want to disable "Display in App Catalog"
- Assignment: You may want to enable "Desired State Management"Step 4: macOS Client – Tests After App Deployment
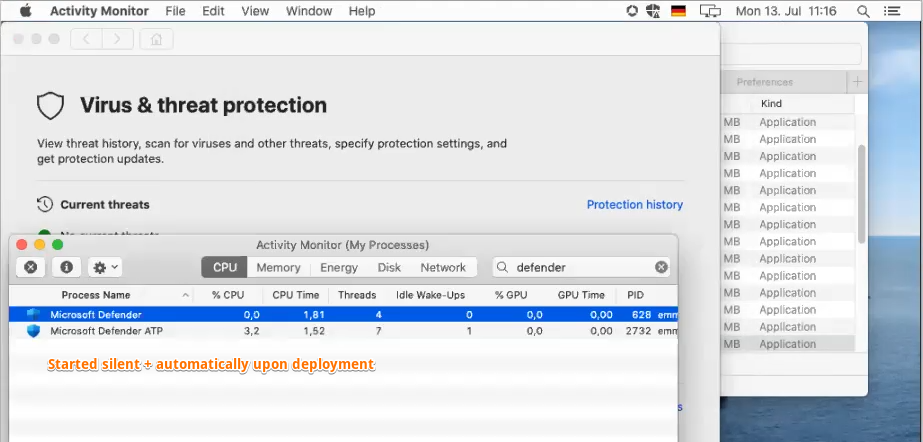
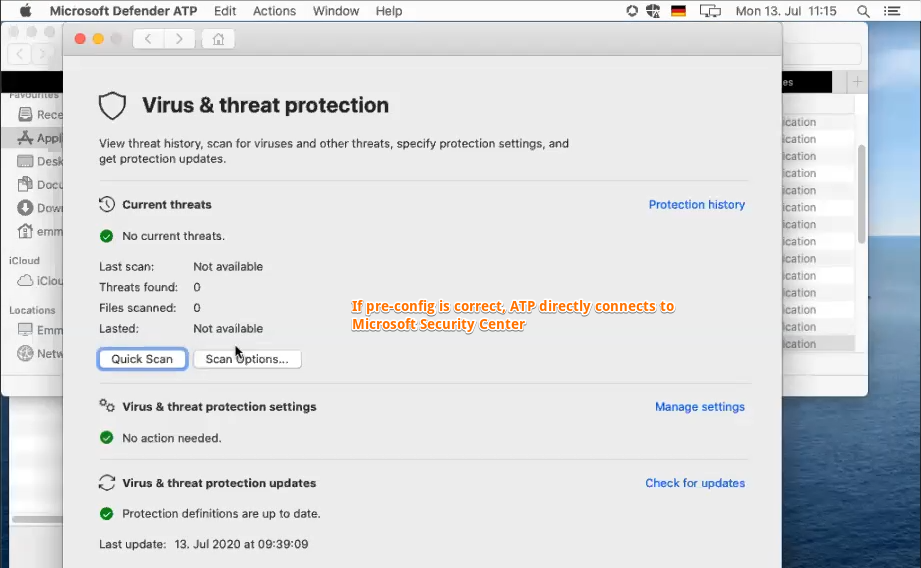
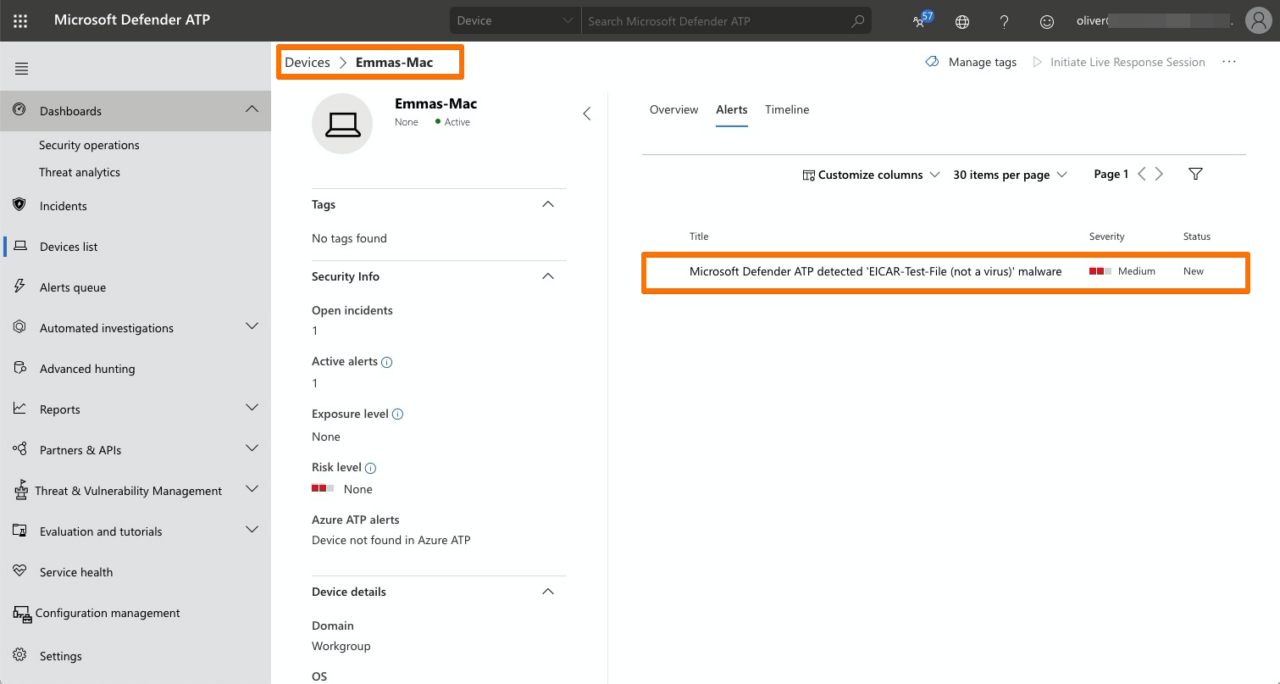
# macOS - Activity Monitor
- Cross check if WAD + ATP app process will show up in Windows Security Center
- You require Microsoft 365 Enterprise subscription. Any EMS E plan is not good enough
# ATP Connectivity Test
Once Microsoft Defender ATP is installed, connectivity can be validated by running the following command in macOS Terminal: mdatp --connectivity-test
# Execute test Thread Detection and reporting to Windows Security Center
curl -o ~/Downloads/eicar.com.txt https://www.eicar.org/download/eicar.com.txt
Helpful URLs
### Microsoft URLs
# Microsoft Security Center
https://securitycenter.windows.com/
# Microsoft Defender Advanced Threat Protection for Mac
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/microsoft-defender-atp-mac
# JAMF-based deployment for Microsoft Defender ATP for Mac
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/mac-install-with-jamf
# Download installation and onboarding packages
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/mac-install-with-jamf#download-installation-and-onboarding-packages
# Set preferences for Microsoft Defender ATP for Mac
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/mac-preferences
### VMware URLs
# VMware Github macOS sample for Microsoft Defender ATP
https://github.com/vmware-samples/euc-samples/tree/master/macOS-Samples/3rd-Party_Software_Guidance/Microsoft-Defender-ATP
# VMware Assistant Packaging Tool to create WS1 UEM deployment metadata
https://resources.workspaceone.com/view/sglgk6r58lbn92jsyqky/en